There are different ways to perform IP based DoS Attacks.The most common IP based DoS attack is that an attacker sends an extensive amount of connection establishment(71)(e.g.TCP SYN requests)to establish hanging connections with the controller or a DPS.Such a way,the attacker can consume the network resources which should be available for legitimate users.In other(72),the attacker inserts a large amount of(73)packets to the data plane by spoofing all or part of the header fields with random values.These incoming packets will trigger table-misses and send lots of packet-in flow request messages to the network controller to saturate the controller resources.In some cases,an(本题)who gains access to DPS can artificially generate lots of random packet-in flow request messages to saturate the control channel and the controller resources.Moreover,the lack of diversity among DPSs fuels fuels the fast propagation of such attacks.Legacy mobile backhaul devices are inherently protected against the propagation of attacks due to complex and vendor specific equipment.Moreover,legacy backhaul devices do not require frequent communication with core control devices in a manner similar to DPSs communicating with the centralized controller.These features minimize both the impact and propagation of DoS attacks.Moreover,the legacy backhaul devices are controlled as a joint effort of multiple network element.For instance,a single Long Term Evilution(LTE)eNodeB is connected up to 32 MMEs.Therefore,DoS/DDoS attack on a single core element will not terminate the entire operation of a backhaul device(75)the network.
Advancements in ( )have contributed to the growth of the automotive industry through the creation and evolution of self-driving vehicles.
In project human resource management , ( )is not a source of power for the project manager.
At the project establishment stage , the feasibility study mainly includes techinical feasibility analysis , ( ), operation environment feasibility analysis and other aspects of feasibility analysis.
( )is a grid that shows the project resources assigned to each work package.
Xinhua News Agency reported in January 2022,Chian will further promote the developmet of a digital economy during the 14th Five-Year Plan eriod(2021-2025). The plan also emphasized industrial ( )transformation.
某公司投资一个使用寿命为5年的项目,第一年年初投入1000万元,从第1年到第5年每年年末都有净现金流量300万元。则项目的静态投资回收期为( )年。
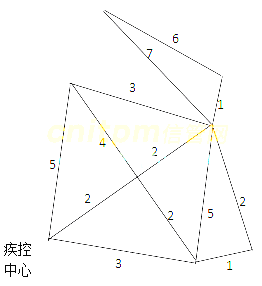
下图是某地的街区网络图(单位:)里),疫情防控期间,一辆消毒车从疾控中心出发,需要消杀所有的街道并返回疾控中心。该消毒车完成消杀工作至少需要运行( )公里 。
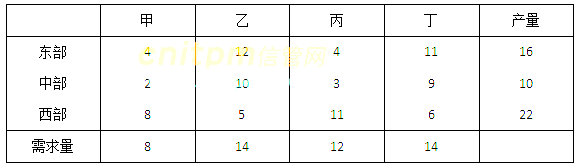
某公司有东部、中部、西部三个生产基地,生产的产品需要运送带甲、乙、丙、丁四个市场,从生产基地到各个市场的单位运价及产量和需求量如表所示,完成该运输任务所需的最小运费为( )。
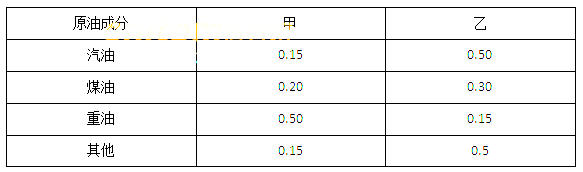
某炼油厂每季度需供应合同单位汽油15吨,煤油12吨,重油12吨,该厂从甲乙两处运回原油提炼,已知两处炼油成分如表所示,从甲处采购原油价格为2000元/吨,乙处为2900元/吨,为了使成本最低,炼油厂应从甲处购15吨,乙处采购( )吨。
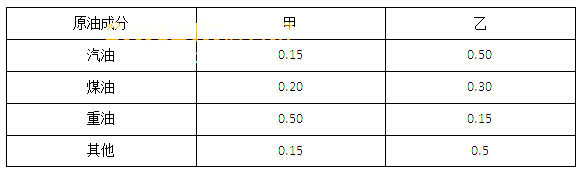
某炼油厂每季度需供应合同单位汽油15吨,煤油12吨,重油12吨,该厂从甲乙两处运回原油提炼,已知两处炼油成分如表所示,从甲处采购原油价格为2000元/吨,乙处为2900元/吨,为了使成本最低,炼油厂应从甲处购( )吨,乙处采购20吨。