下面关于数字签名的说法中,不正确的是()。
数字签名使用公钥算法,
整个数字签名应用过程很简单:
1.信息发送者使用一单向散列函数对信息生成信息摘要;
2.信息发送者使用自己的私钥签名信息摘要;
3.信息发送者把信息本身和已签名的信息摘要一起发送出去;
4.信息接收者通过使用与信息发送者使用的同一个单向散列函数对接收的信息本身生成新的信息摘要,再使用信息发送者的公钥对信息摘要进行验证,以确认信息发送者的身份是否被修改过。
5.接受者只需使用发送者的公钥对信息摘要进行解密。
整个过程中,接收方不需要使用发送方的私钥。因此C不正确。
Data security is the practice of protecting digital information from ( )access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the ( )security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational ( )and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should ( )the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like (作答此空),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
Data security is the practice of protecting digital information from ( )access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the ( )security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational ( )and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should (作答此空)the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like ( ),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
Data security is the practice of protecting digital information from ( )access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the ( )security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational (作答此空)and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should ( )the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like ( ),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
Data security is the practice of protecting digital information from ( )access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the (作答此空)security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational ( )and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should ( )the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like ( ),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
Data security is the practice of protecting digital information from (作答此空)access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the ( )security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational ( )and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should ( )the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like ( ),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
以下关于项目风险管理的说法中,不正确的是( )。
某分公司财务 PC 通过专网与总部财务系统连接,拓扑如图8所示。某天,财务PC访问总部财务系统速度缓慢、时断时好,网络管理员在财务PC端ping总部财务系统,发现有网络丢包,在光电转换器1处ping总部财务系统网络丢包症状同上,在专网接入终端处ping 总部财务系统,网络延时正常无丢包,光纤1两端测得光衰为-28dBm,光电转换器1和2指示灯绿色闪烁。 初步判断该故障原因可能是( ),可采用(作答此空)措施较为合理。
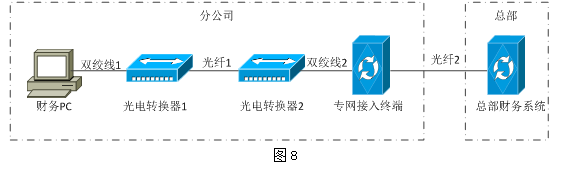
某分公司财务 PC 通过专网与总部财务系统连接,拓扑如图8所示。某天,财务PC访问总部财务系统速度缓慢、时断时好,网络管理员在财务PC端ping总部财务系统,发现有网络丢包,在光电转换器1处ping总部财务系统网络丢包症状同上,在专网接入终端处ping 总部财务系统,网络延时正常无丢包,光纤1两端测得光衰为-28dBm,光电转换器1和2指示灯绿色闪烁。 初步判断该故障原因可能是(作答此空),可采用( )措施较为合理。
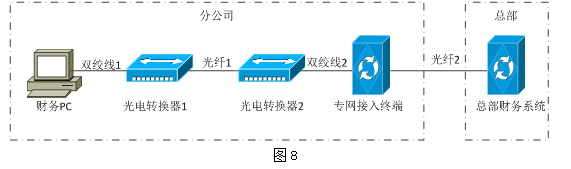
某主机可以ping 通本机地址,而无法ping通网关地址,网络配置如图7所示,造成该故障的原因可能是( )。
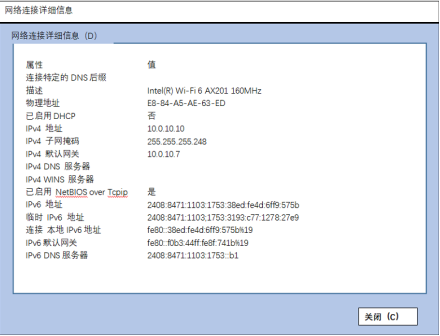
下列命令片段用于配置( )功能。