Network security is the protection of the underlying networking infrastructure from ( )access, misuse, or theft, It involves creating a secure infrastructure for devices, users and applications to work in a ( ) manner. Network security combines multiple layers of defenses at the edge and in the network. Each network security layer implements ( ) and controls. Authorized users gain access to network resources. A ( ) is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. A virtual (作答此空) network encrypts the connection from an endpoint to a network, often over the internet. Typically a remote-access VPN uses IPsec or Secure Sockets Layer to authenticate the communication between device and network.
网络安全是保护底层网络基础设施免受非授权访问、误用或盗窃,它涉及为设备、用户和应用程序创建一个安全的基础设施,使其以安全方式工作。网络安全结合了边缘和网络中的多层防御。每个网络安全层实现策略和控制。授权用户可以访问网络资源。防火墙是一种网络安全设备,用于监控传入和传出的网络流量,并根据定义的一组安全规则决定是否允许或阻止特定的流量专用网络通常通过internet对端点到网络的连接进行加密。通常,远程访问VPN使用IPsec或安全套接字层来验证设备和网络之间的通信。
Data security is the practice of protecting digital information from ( )access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the ( )security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational ( )and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should ( )the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like (作答此空),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
Data security is the practice of protecting digital information from ( )access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the ( )security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational ( )and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should (作答此空)the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like ( ),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
Data security is the practice of protecting digital information from ( )access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the ( )security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational (作答此空)and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should ( )the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like ( ),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
Data security is the practice of protecting digital information from ( )access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the (作答此空)security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational ( )and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should ( )the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like ( ),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
Data security is the practice of protecting digital information from (作答此空)access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the ( )security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational ( )and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should ( )the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like ( ),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
以下关于项目风险管理的说法中,不正确的是( )。
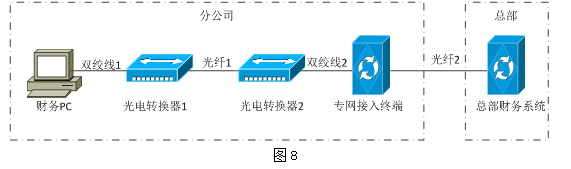
某分公司财务 PC 通过专网与总部财务系统连接,拓扑如图8所示。某天,财务PC访问总部财务系统速度缓慢、时断时好,网络管理员在财务PC端ping总部财务系统,发现有网络丢包,在光电转换器1处ping总部财务系统网络丢包症状同上,在专网接入终端处ping 总部财务系统,网络延时正常无丢包,光纤1两端测得光衰为-28dBm,光电转换器1和2指示灯绿色闪烁。 初步判断该故障原因可能是( ),可采用(作答此空)措施较为合理。
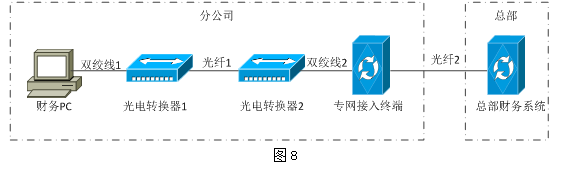
某分公司财务 PC 通过专网与总部财务系统连接,拓扑如图8所示。某天,财务PC访问总部财务系统速度缓慢、时断时好,网络管理员在财务PC端ping总部财务系统,发现有网络丢包,在光电转换器1处ping总部财务系统网络丢包症状同上,在专网接入终端处ping 总部财务系统,网络延时正常无丢包,光纤1两端测得光衰为-28dBm,光电转换器1和2指示灯绿色闪烁。 初步判断该故障原因可能是(作答此空),可采用( )措施较为合理。
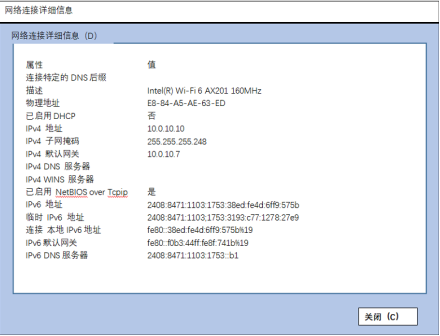
某主机可以ping 通本机地址,而无法ping通网关地址,网络配置如图7所示,造成该故障的原因可能是( )。
下列命令片段用于配置( )功能。